Forward local internet through ssh tunnel
Install http proxy on local machine, and bind it to port 8080
ssh -R 8080:<local IP>:8080 user@<remote IP> export http_proxy=http://<local IP>:8080 export https_proxy=http://<local IP>:8080 sudo visudo #append text Defaults env_keep = "http_proxy https_proxy ftp_proxy"
Now wget will work and so will sudo apt-get so you can install packages.
Just adding some more and clear steps
Do the setup as follows:
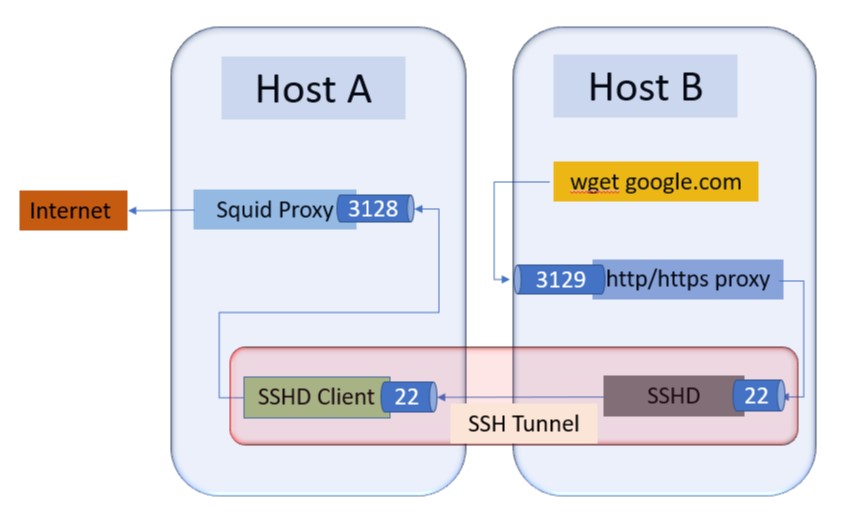
Setup on Host A:
- Install proxy server Squid on Host A . By default Squid listens on port 3128.
- yum install squid
- Comment the http_access deny all then add http_access allow all in /etc/squid/squid.conf
- If Host A itself uses some proxy say 10.140.78.130:8080 to connect to internet then also add that proxy to /etc/squid/squid.conf as follows:
refresh_pattern (Release|Packages(.gz)*)$ 0 20% 2880 cache_peer 10.140.78.130 parent 8080 0 no-query default never_direct allow all
Setup on Host B:
- Add the following entries to /etc/environment
export http_proxy=http://127.0.0.1:3129 export https_proxy=http://127.0.0.1:3129
- source /etc/environment
Now our setup is complete.
Creating SSH tunnel with Remote port forwarding
- Run the following SSH command from Host A: ssh -R 3129:localhost:3128 user@HostB
- If you want to make persistent SSH tunnel, you can use autossh as follows: autossh -M 20000 -f -NT -R 3129:localhost:3128 user@HostB
- For above autossh command to work, you should be having SSH Keys setup from HostA to HostB
- This will allow Host B to access the internet through Host A.
Checking the internet:
- Run the following command from Host B: wget https://google.com
Traffic flow diagram :